

Uhh do we know if this extends to sites.google.com?


Uhh do we know if this extends to sites.google.com?


My professor made me install TeamViewer to our lab computers despite strong pushback from me, and perfectly functioning ssh access through the campus VPN. I can’t wait to send this to him.


I’ve been using them on both my phone and desktop, works great!


I have and use a Microsoft account. I would always setup my computer offline because I don’t want my home folder to be called "myema"il@email.com
Seriously who thought that was a good idea? Your account literally has your name tied to it, call it that!


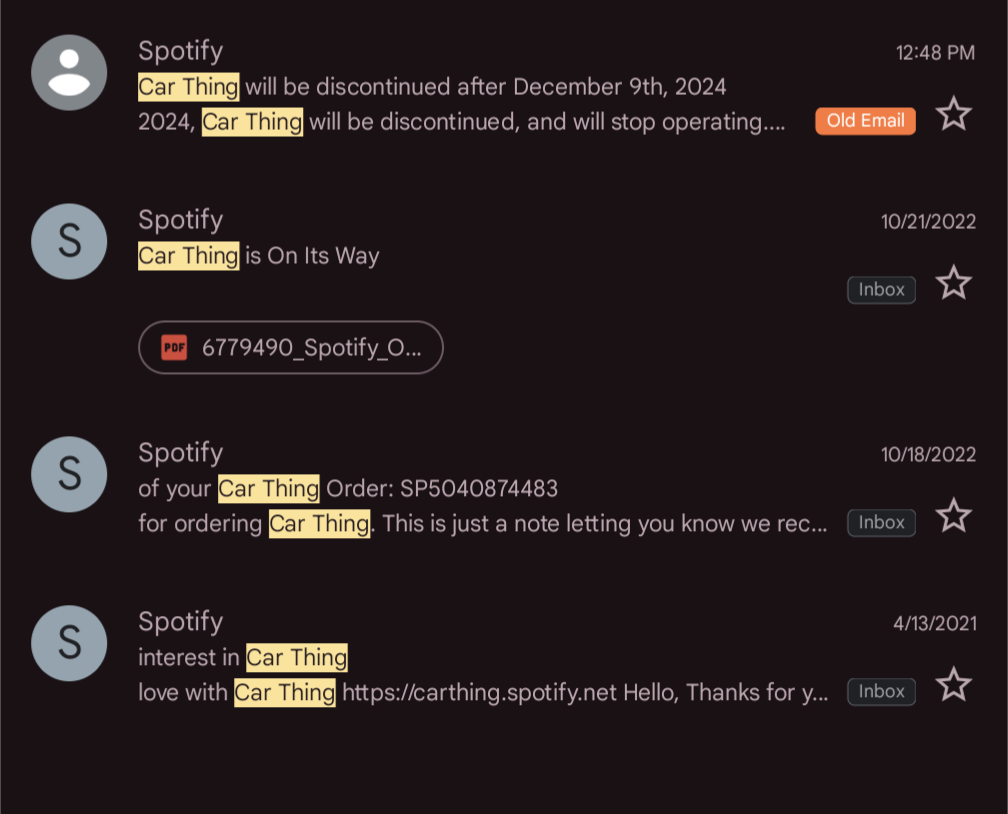
Even Google products have a longer lifespan 😖
I’ve since moved on to Tidal. Bought it at $30 when root mods started to be developed, but never really went anywhere.
Image alt:


As a Thinkpad user since the early 2000s, I’m extremely excited to see this news after I’ve slowly watched all of my repair & upgrade ability be removed.
I’ve heard the 24.04 installer is having issues. I would hold off for an update for them to patch other stuff as well


Not on fedora, but on Neon with a 3070. KDE 6 will lock up on Xorg, while electron apps will flash on Wayland, though there is a flag to enable Wayland support, it keeps dropping off of discord every time it updates. Running nvidia 550 proprietary, haven’t gotten to use the open ones yet as I need cuda for work


I am not as worried about DMCA as the author is lol


Is 1337x.to not the real one? I’ve seen it on there too


I’ll have to look into this a bit more. The guy at the end of the comment chain says his chromium stuff is still flickering, but I’ll give it a whirl when I don’t strictly need a working dev environment :P


Had to switch back to X11 because of novideo being shit. Tried 525, 535, and 540 and vscode would flicker like that one light at the back of the gas station nobody likes to visit because all they sell are stale cigarettes


If you don’t want to buy a domain you can try a reverse DNS lookup, your ISP may already give you one. Mine was C-XX-XX-XX-XX.hsd1.pa.comcast.net and I could get a let’s encrypt certificate with that. I did end up buying a domain but it was good for personal use


I can load a pirated copy onto a modded console, does that mean that Nintendo is liable for their software being used for piracy?


Edge has done this by default since release, with an option to be more strict in what it blocks


Glad to hear it worked! I edited the comment in case anybody stumbles across it with the same issue


It’s not “best practice”, but a compromised key is a compromised key whether that key is used to connect 1 or 100 computers to a server. No, I can’t shut off access to exactly one machine, I do not however have any difficulty in shutting off access to every machine and replacing it with a new key. Your system and my system are no different with a single compromised key.
If I had 100 computers that I had to change identity files on each time it was compromised, and my keys were being compromised often, I would see a benefit from using multiple different keys.
Quit acting like I’ve left the front door to my house open when the door is locked but my roommate and I share the same key.


This is actually quite handy, I’ve got a yubikey already and didn’t know they could be used for ssh


Again, I know it’s not amazing security but it’s not inherently bad. The key (actually encrypted), if (not when) compromised would provide the same level of access to my system as having two keys with one compromised. Assuming I’m an all knowing wizard and can smell when a key is compromised, I can log in remotely and replace the old key with a freshly generated one. More likely however is that if anybody was going to actually do something with my compromised key, they’d clear my authorized_keys file and replace it with a key I don’t have access to. Don’t kid yourself into thinking having multiple keys suddenly makes you 10x more secure.
What’s more likely is someone finds my flashdrive on the ground, goes “oh boy free flashdrive full of Linux ISOs and recovery tools!” And proceeds to wipe it and use it for their own shit, while I regenerate a new key when I notice it missing.
This is just a theory, I don’t have knowledge of the inner-workings of either Linux or Windows (beyond the basics). While Microsoft has been packing tons of telemetry in their OS since Windows 10, I think they fucked up the I/O stack somewhere along the way. Windows used to run well enough on HDDs, but can barely boot now.
This is most easily highlighted by using a disk drive. I was trying to read a DVD a while ago and noticed my whole system was locked up on a very modern system. Just having the drive plugged in would prevent windows from opening anything if already on, or getting past the spinner on boot.
The same wasn’t observed on Linux. It took a bit to mount the DVD, but at no point did it lock up my system until it was removed. I used to use CDs and DVDs all the time on XP and 7 without this happening, so I only can suspect that they messed up something with I/O and has gone unnoticed because of their willingness to ignore the issues with the belief they’re being caused by telemetry